Unleashing The Power Of Code Hardening Techniques: Level Up Your Security Now!
Code Hardening Techniques
Introduction
Greetings, Readers!
Welcome to this article on code hardening techniques. In this digital age, securing our software applications and systems is of utmost importance. Code hardening plays a crucial role in protecting our software from potential vulnerabilities and attacks. In this article, we will explore various techniques and best practices to enhance the security of our code and safeguard our applications. So, let’s dive in!
1 Picture Gallery: Unleashing The Power Of Code Hardening Techniques: Level Up Your Security Now!
In this article, we will cover the following topics:
What are code hardening techniques and why are they important?
Who should implement code hardening techniques?
When should code hardening techniques be applied?
Where can code hardening techniques be utilized?
Why should developers consider code hardening techniques?
How can code hardening techniques be implemented effectively?
What are Code Hardening Techniques?

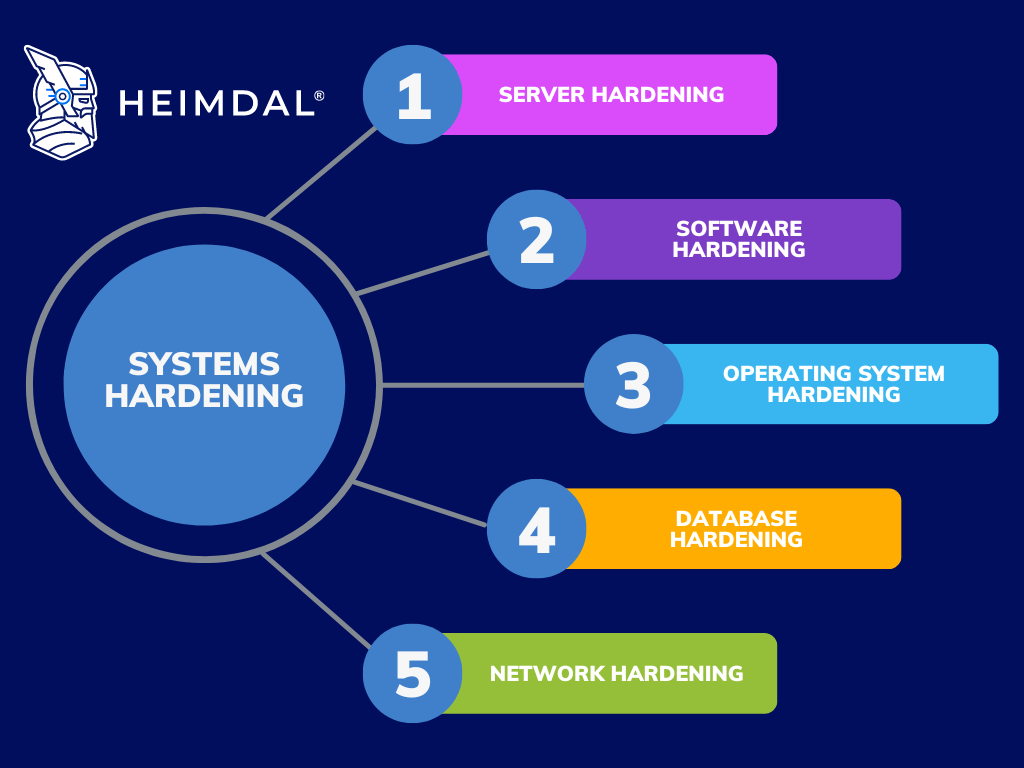
Image Source: heimdalsecurity.com
🔒 Code hardening techniques refer to a set of practices and strategies implemented to strengthen the security of software code. These techniques aim to minimize vulnerabilities and protect the code from potential threats and attacks. By implementing code hardening techniques, developers can ensure that their applications are resilient and less prone to security breaches.
There are several code hardening techniques available, including:
Input validation
Code obfuscation
Anti-debugging techniques
Memory protection mechanisms
Secure coding practices
Software patching and updates
Application sandboxing
Now, let’s take a closer look at who should implement these techniques.
Who Should Implement Code Hardening Techniques?
👥 Code hardening techniques should be implemented by software developers, security engineers, and anyone involved in the development and maintenance of software applications. It is the responsibility of these individuals to ensure the integrity and security of the code they create or manage.
Whether you are developing a simple mobile application or a complex enterprise software, code hardening techniques should always be considered. By implementing these techniques, developers can protect their code and prevent potential security breaches.
Now that we know who should implement these techniques, let’s explore when they should be applied.
When Should Code Hardening Techniques be Applied?
⏰ Code hardening techniques should be applied throughout the entire software development lifecycle. It is essential to consider security aspects from the initial design phase to the deployment and maintenance stages.
By integrating code hardening techniques as early as possible, developers can minimize the risk of vulnerabilities and ensure that security is an integral part of the software development process. This proactive approach helps in reducing potential security flaws and saves valuable time and effort in the long run.
Now that we have covered the importance of code hardening techniques and when to apply them, let’s discuss where these techniques can be utilized.
Where Can Code Hardening Techniques be Utilized?
🌍 Code hardening techniques can be utilized in various software environments, including:
Web applications
Mobile applications
Desktop applications
Embedded systems
Cloud-based applications
Client-server architectures
Regardless of the software environment, code hardening techniques should be implemented to protect the code and ensure the security of the application.
Now that we know where code hardening techniques can be utilized, let’s delve into the reasons why developers should consider implementing these techniques.
Why Should Developers Consider Code Hardening Techniques?
❓ Developers should consider code hardening techniques for the following reasons:
To protect sensitive data: Code hardening techniques help in safeguarding sensitive data, such as user information, financial details, or intellectual property from unauthorized access.
To prevent code tampering: Implementing code hardening techniques makes it difficult for attackers to modify or tamper with the code, reducing the risk of malicious activities.
To defend against attacks: By implementing code hardening techniques, developers can fortify their applications against various attacks, including injection attacks, buffer overflows, and cross-site scripting.
To comply with regulations: In many industries, there are strict regulations and compliance requirements. Code hardening techniques can help developers meet these requirements and ensure the security of their applications.
To build trust: Implementing code hardening techniques demonstrates a commitment to security, improving the trustworthiness of the application among users and stakeholders.
Now that we understand the importance of code hardening techniques, let’s move on to the implementation aspect.
How Can Code Hardening Techniques be Implemented Effectively?
🔐 To implement code hardening techniques effectively, developers should consider the following steps:
Perform a thorough code review: Analyze the codebase for any potential vulnerabilities and identify areas that require hardening.
Apply secure coding practices: Follow industry best practices, such as input validation, secure error handling, and proper memory management.
Implement code obfuscation: Obfuscate the code to make it difficult for attackers to understand its logic and reverse engineer it.
Employ anti-debugging techniques: Implement measures to prevent or detect debugging attempts, making it harder for attackers to analyze the code during runtime.
Utilize memory protection mechanisms: Employ technologies like Address Space Layout Randomization (ASLR) and Data Execution Prevention (DEP) to protect the application’s memory from exploitation.
Regularly update and patch the software: Stay up to date with the latest security patches and updates to address any known vulnerabilities.
Test the application thoroughly: Perform rigorous security testing, including penetration testing, to identify and fix any weaknesses.
By following these steps, developers can effectively implement code hardening techniques and enhance the security of their applications.
Frequently Asked Questions (FAQ)
1. Can code hardening techniques guarantee 100% security?
No, code hardening techniques cannot guarantee 100% security. However, they significantly reduce the risk of vulnerabilities and make it harder for attackers to exploit the code.
2. Are code hardening techniques only applicable to large-scale applications?
No, code hardening techniques are applicable to applications of all sizes. Whether it is a small mobile app or a large-scale enterprise system, code hardening techniques should be considered to ensure the security of the application.
3. Do code hardening techniques impact the performance of the application?
Code hardening techniques may have a slight impact on the performance of the application. However, the benefits of enhanced security outweigh the minimal performance impact.
4. Are code hardening techniques a one-time implementation?
No, code hardening techniques should be an ongoing effort. As new security threats emerge, developers need to stay updated and implement additional measures to counter these threats.
5. Can code hardening techniques replace other security measures?
No, code hardening techniques should be used in conjunction with other security measures, such as network security, access control, and encryption. A multi-layered security approach provides a more robust defense against potential attacks.
Conclusion
In conclusion, code hardening techniques play a crucial role in securing software applications from potential vulnerabilities and attacks. By implementing these techniques, developers can protect sensitive data, prevent code tampering, defend against attacks, comply with regulations, and build trust among users and stakeholders.
Remember, code hardening techniques should be applied throughout the software development lifecycle, from the initial design phase to the deployment and maintenance stages. By following best practices, such as code review, secure coding, code obfuscation, and regular updates, developers can effectively implement code hardening techniques and enhance the security of their applications.
So, don’t overlook the importance of code hardening techniques. Start implementing them today to safeguard your software and ensure a secure digital environment for your users.
Final Remarks
📝 The information provided in this article is intended for educational purposes only. The effectiveness of code hardening techniques may vary based on specific contexts and requirements. It is advisable to consult with security professionals and follow industry best practices to ensure the security of your software applications.
This post topic: Programming